World Backup Day, observed on March 31st annually, serves as a designated occasion to underscore the critical importance of regular data backups for ensuring data continuity. Although this day effectively highlights a fundamental best practice, we firmly advocate for a continuous commitment to maintaining and safeguarding backups rather than confining such awareness to a single day.
Telesys Voice and Data Blog
In business, there are always issues that need to be met. Often, there are so many that finding which ones to give priority is a chore all in itself. Choosing the best path forward depends on the situation, so when you are considering your organization’s disaster recovery you have to take into account every troubling situation your business can encounter. This month let’s go through some of the most prevalent disasters that a business can face.
Running a business is stressful, but so is thinking about a future where that business (and its data) no longer exists. If you’re not careful with your preparedness, you could stare down a disaster with no hopes of recovery. This is why we urge you to take proactive action now—so you can prevent these kinds of scenarios from taking your business off the market for good.
For modern organizations that depend highly on their technology, nothing is quite so scary as an event that can completely marginalize its ability to operate. This doesn’t need to be a fire, flood, or some other major cataclysm; it could be something as simple as some of your old IT fails and you’re not ready for it. This week, we thought we’d briefly go through what a catastrophic failure looks like and some steps you can take to keep your business from experiencing one.
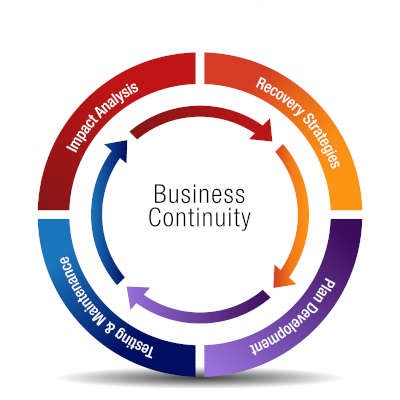
When considering a continuity plan for your business, you need to consider some scenarios that may not ever happen. This is called risk management and it is the basis of keeping your business up and running regardless of the situations that it encounters. This month, we thought we would outline some of the variables that need to be addressed when creating a comprehensive business continuity plan.
All businesses store and transmit data on a regular basis. From financial spreadsheets to client information to employee records, there is no shortage of data required by most organizations to maintain operations. What would you do if all that data were to suddenly vanish into thin air, or worse, be stolen by hackers?
Businesses were just hit with one of the worst disasters possible, and many of them were not prepared. It’s not often that a global pandemic hits, but businesses that were prepared to react to it were much more successful than ones that were forced to shoot from the proverbial hip. So while many businesses were overrun with new costs brought forth by the pandemic, the businesses that considered a situation like the one we’ve been facing for well over a year, and had a strategy for what they needed to accomplish to keep continuity during an event such as the COVID-19 pandemic, are faring quite a bit better than those that didn’t have a plan. This month we thought we’d outline a few ways your business can improve its disaster preparedness.
When considering a continuity plan for your business, you need to consider some scenarios that may not ever happen. This is called risk management and it is the basis of keeping your business up and running regardless of the situations that it encounters. This month, we thought we would outline some of the variables that need to be addressed when creating a comprehensive business continuity plan.
The Novel Coronavirus has made its way around the world and it has certainly changed the way a lot of businesses do things. Some businesses have put in some type of disaster recovery platform. This is basically a plan for returning to continuity after some type of disaster, but we are seeing that many business continuity plans were not broad enough to take on a worldwide pandemic. Sadly, many of these businesses won’t open again.
Few organizations take business continuity planning as serious as financial organizations do. The Federal Reserve Bank (FRB) and Securities and Exchange Commission (SEC), as well as the organizations they oversee, depend heavily on technology for their daily operations. For these establishments, a severe data loss event or significant downtime has the potential to cripple the economy, depending on the severity. As such, they require all of the institutions that they have jurisdiction over to meet certain business continuity benchmarks.
You might hear the term “zero-day” when discussing security threats, but do you know what they actually are? A zero-day threat is arguably one of the most devastating and dangerous security issues your business could face, and if you’re not prepared, they could be the end of it.
Let me ask you this: does your business have a dedicated data backup and disaster recovery system? If not, we need to talk. A comprehensive backup and disaster recovery platform (BDR) can turn out to be one of the most critical parts of managing a business’ IT infrastructure. By having a plan to turn to in the event a serious problem such as ransomware or a natural disaster descends upon your business, you can be better prepared.
You don’t need to be repeatedly told just how important risk management is. If you did, you probably wouldn’t have made it this far. One problem you see from business owners today is that while they understand just how many problems there are--and which ones they need to find solutions for first--they want to grow their company so fast that they overlook potential problems and end up hurting their business as a result. This month, we thought we would talk a little bit about contingency planning and how, if it is done right, it can have a marked effect on your business’ ability to carry-on after a problematic event.
For the modern business, ensuring that you have contingencies in place will go a long way toward keeping you in business if disaster strikes. One of the contingencies many businesses choose to make as part of a business continuity strategy is a disaster recovery plan. Disaster recovery is more than restoring data, it can mean mobilizing people and capital against time. Let’s take a look at two of the core components of a comprehensive disaster recovery strategy, Recovery Time Objective and Recovery Point Objective.
Businesses need to be extremely careful about how they protect their interests, but just in case something unfortunate happens, you want to have measures in place to guarantee that your future is secure. To this end, data backup and disaster recovery is critical. We’ll walk you through what you need to know about implementing data backup and disaster recovery, including the best way to make it happen.
Let’s face it; nobody wants to talk about disaster recovery, as even invoking these words makes the possibility a reality. Unfortunately, this is something that has to be discussed, as your business depends on it. This might seem like hyperbole, but if you knew what is at stake, you’d likely agree with us.
These days most consumers lean heavily on their payment cards. Whether they use credit cards, debit cards, or gift cards, consumers today are much more apt to use their card then they are to use cash. Why is this? Convenience mostly, but also there is a belief that using a payment card is more secure than walking around with a wad of cash in your pocket. Today, we will get to the bottom of the matter.
By now, you’ve probably heard about the importance of business continuity and disaster recovery planning for small businesses. According to FEMA, more businesses have business continuity plans than ever before. With so many SMBs looking to secure their future, there are still a few aspects of business continuity planning that today’s business need to comprehend. After all, there is more to it than just data backup. Disaster recovery is something that needs to be planned, practiced and updated.
Cybersecurity is a big point of emphasis for the modern IT administrator. For the private business, it’s important for enough to be done in order to secure the business’ assets, and the integrity of the network itself. Unfortunately, when looking at public computing resources, there isn’t enough talent available to properly secure the systems that government entities rely on.
What would happen if you were in the middle of typing a report or performing some task, and the office suddenly lost power? Too many would find themselves staring blankly at an equally blank screen as their infrastructure suddenly ceased operations. However, there is a device that can help save you from the worst effects of sudden power loss.
Mobile? Grab this Article!
Tag Cloud